The internet moves on and the next big thing that gets dropped is the support for older versions of TLS (Transport Layer Security). If you not already have done so, now would be a good time to check that your server understands TLS 1.2 and disable the older versions of TLS on your web servers.
A few months back I did a write-up on how to do get TLS 1.2 on a Windows Server 2008 R2. The same commands and registry keys help you to get rid of the old protocols on newer versions of Windows Server as well.
A simple way to check the configuration of your server is to enter your domain into the SSL Server Test from Qualys. After a few minutes you should see a detailed report that shows you the health of your server. In the configuration section you find the supported protocols of your server (here TLS 1.0, 1.1 and 1.2 are active):
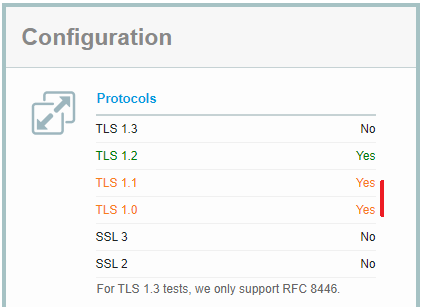
When TLS 1.2 is active, you can safely disable all the other protocols. However, if TLS 1.2 is not active, you first need to activate it. Otherwise your users will no longer be able to connect to your web server.
Before you make any changes to the registry, you must make a backup. If something goes wrong, you can go back and do not need to reinstall your server.
You can copy these lines in a file ending with *.reg and execute it:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server]
“DisabledByDefault”=dword:00000001
“Enabled”=dword:00000000
|
If everything works you should get a success message at the end. To activate these changes, you now need to reboot your server.
As soon as your website is back up, you can rerun the SSL Server Test. If you get the exact same result back, you need to clear the cache by clicking on the link with that text right at the top. Now you should get a much better result and all the old protocols should be disabled:
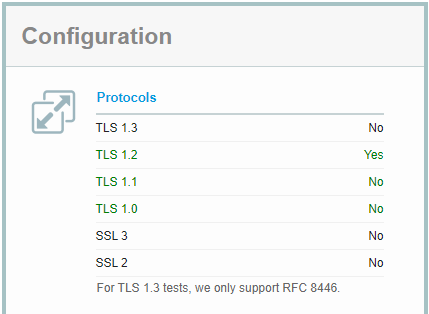
With this little changes your Windows Server is now ready for the changes in the browsers that will rollout over the next weeks. Unfortunately, you cannot disable the old protocols on all your Windows Server.

